Flight – and bite – of the Dragon
Against the backdrop of Syrian airstrikes, the US’s allies are bracing themselves for crippling online attacks that could bring down essential infrastructure including energy supplies and gas networks. A resurgence of energy cyber-attacks has been linked to ‘Dragonfly’, a highly advanced online espionage group, reportedly with roots in Russia. Energy Networks Australia CEO, Andrew Dillon, recently attended 2018’s International Electricity Summit in Washington that considered the global response – including the work of energy networks in Australia – to cyber security threats.

Fig 1[1].
The dragonfly is a creature of intrigue, its appearance and behaviour fascinating to many cultures and civilisations. Universally, the dragonfly symbolizes power and poise through its ability to move in all six directions at amazing speeds with graceful agility. The name Dragonfly has its source in the myth that Dragonflies were once Dragons, thus the genus name ‘Odonata’ meaning ‘tooth’.

The espionage group ‘Dragonfly’, infamous for its attacks on energy security systems, has resurged to take some vicious bites.
Late last year, Symantec[2] reported that Dragonfly, suspected to have its roots in Russia, was targeting Europe’s and North America’s energy sectors in a new wave of cyber attacks. The group, in operation since at least 2011, re-emerged as “Dragonfly 2.0”.

Issues relating to cyber-security are generally considered by the public to be a financial services and privacy concern: credit card fraud, identity theft. What many people never think about is an attack in the energy space. A compromised grid could bring a city (or country) to its knees if essential infrastructure and services are cut: water, electricity, gas supplies, hospitals, transport. Recent global events have forced the doomsday scenario to the fore with politicians and sector leaders speaking publicly with unprecedented candour and immediacy.
Putin’s recent warning to Great Britain was stark: there are incumbent “consequences” to be suffered for the Syrian air strikes. In response, Britain’s Foreign Secretary, Boris Johnson, raised the alarm, saying an imminent cyber backlash could see Britain’s vital services affected.
“’You have to take every possible precaution, and when you look at what Russia has done, not just in this country…attacks on critical national infrastructure – of course we have to be very, very cautious indeed[3].”
Johnson warned that cyber attacks undermine “civilised values” fearing that hackers could force electricity blackouts and cripple the grid. A few weeks prior, an industry taskforce was announced to draw up a strategy to restore the grid in the event of a nationwide power failure triggered by a cyber-attack[4].
This week the UK’s Energy Networks Association took the extraordinary step of putting out a media release to refute claims there was a spike in the number of power cuts over the weekend of the airstrikes in Syria as a result of cyber-attacks[5].
Ciaran Martin, director of the National Cyber Security Centre (NCSC), the public face of UK spy agency Government Communications Headquarters (GCHQ), confirmed that Moscow’s attempts at hacking into the UK’s energy network over the last year was part of a larger effort seeking to undermine the international system’s critical infrastructure[6], suggesting it is a matter of ‘when’, rather than ‘if’[7].
Jeremy Fleming, GCHQ’s director, launched a blistering attack on the Kremlin, simultaneously warning that the online threat from Moscow was ill addressed at peril.
“The Russian government widely uses its cyber capabilities. They’re not playing to the same rules, they’re blurring the boundaries between criminal and state activity.[8]
“To stay ahead, to match the pace of technological change, we are investing in deploying our own cyber toolkit. It’s one that combines offensive and defensive cyber capabilities, to make the UK harder to attack, better organised to respond when we are, and able to push back if we must.[9]”
“We may look to deny service, disrupt a specific online activity, deter an individual or a group or perhaps destroy equipment and networks.[10]”
A Cold War in cyberspace
The threat posed by Dragonfly isn’t just a threat for European countries; the United States has been on cyber threat alert for some time, particularly since the allegations of Russian interference in the 2016 Presidential election[11].
In the energy sector, the North American Electric Reliability Corporation (NERC) set up the Electricity Information Sharing and Analysis Center (E-ISAC) in 1999. Originally focused on physical security, in recent years E-ISAC has greatly broadened its remit to provide unique insights, leadership, and collaboration, particularly on high impact low frequency (HILF) events.
An ongoing challenge is the unknown nature of what each attack may involve; a coordinated attack could be a combination of physical and cyber threats, and this underlines the need for a collaborative, cross agency approach. E-ISAC has undertaken four biennial GridEx grid security exercises. GridEx is an unclassified public/private exercise designed to simulate a coordinated cyber/physical attack with operational impacts on electric and other critical infrastructures across North America and beyond, in order to bolster preparedness, resiliency and reliability.
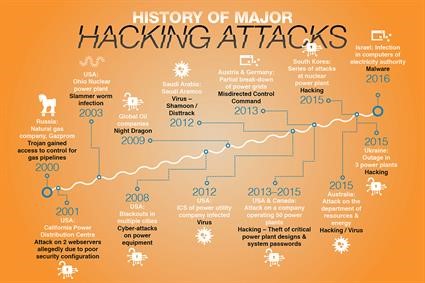
Fig 4[12] – History of attacks in the energy sector
Cyber-attacks in our space have been foreseen. A 2015 survey of 625 IT executives in the U.S., U.K., France, and Germany found that 48 percent thought a cyber-attack on critical infrastructure, including energy infrastructure, by the year 2018 resulting in loss of life was likely[13].
Is Australia safe from the Dragonfly’s bite?
Our new Minister for Law Enforcement and Cyber Security, Angus Taylor, warned that in our efforts to thwart the Dragonfly, businesses, agencies and departments mustn’t entrench silos even further, but should collaborate and share.
“The key in cyber, like most areas, is speed and that means you’ve got to share information in a collaborative way.[14]”

Fig 5[15].
At March’s Senate committee examining the digital delivery of government services, Australian Signals Directorate (ASD) director-general Mike Burgess berated department heads for being secretive when it comes to cyber-security.
“There is a possibility that those who aren’t taking this seriously don’t ask for our help. That would be a risky strategy for any chief executive[16].”
Last year, Australia launched a national $230 million cyber security strategy, led by attorney general George Brandis, with particular attention on the energy sector. Securing critical infrastructure assets in partnership with industry was a key focus.
“With increased foreign involvement, through ownership, offshoring, outsourcing and supply chain arrangements, Australia’s national critical infrastructure is more exposed than ever to sabotage, espionage and coercion,” Mr Brandis said[17].
While legislative steps have been put in place to protect critical infrastructure, what is industry doing to protect its assets?
Energy Networks Australia’s role
The Finkel Review’s examination of the future of Australia’s National Electricity Market (NEM) recommended a heightened emphasis on cyber security, with an annual report considering the NEM’s cyber security preparedness.
The review also recommended an Energy Security Board (ESB) that would co-ordinate whole-of-system monitoring of security, reliability and planning. The ESB was established in late 2017 and espousing collaboration, works with key agencies including the Australian Cyber Security Centre, the Critical Infrastructure Centre, the Department of Defence, ASD, ASIO, and Prime Minister and Cabinet.
The Federal Government and AEMO have ultimate responsibility for the sector’s response to cyber threats, however, Energy Networks Australia has designed programs to complement and add value to those work streams.

Energy Networks Australia’s cyber-security program is, together with our members, reviewing networks’ resilience and capacity, with a final report expected in June 2018. Litmus, the independent consultant leading the study is utilising the internationally recognised US Department of. Energy’s Cyber security Capability Maturity Model (C2M2) assessment tool.
Networks are collaborating with AEMO (which has ultimate responsibility for our nation’s grid security) to ensure the findings of our program can be used to inform the Cyber Security Industry Working Group (CSIWG) and mitigate threats.
Networks are also working with Standards Australia to undertake a review of technical standards and international protocols. A future roadmap will consider the most appropriate technical cyber standards for Australia. Examining how our nation’s information and technology planning matches up with international standards will complement the Cyber Security Industry Working Group task to develop a holistic cyber security framework for Australia.
Energy Networks 2018 conference in June will take a deep dive into cyber security and leaders in our sector will share how we can best protect our assets.
The adage about an ounce of prevention being worth of a pound of cure is apt in relation to cyber security; the strongest insect repellent we have to stymie the Dragonfly is continued information sharing, timely communication, cross agency working and agile, expedient solutions.
[3] https://www.telegraph.co.uk/politics/2018/04/15/boris-johnson-warns-uk-must-take-every-possible-precaution-amid/
[5] http://www.energynetworks.org/news/press-releases/2018/april/ena%E2%80%99s-response-to-concerns-regarding-cyber-security-attacks-on-great-british-energy-networks.html
[6] https://www.telegraph.co.uk/news/2017/11/15/russian-hackers-have-targeted-britains-energy-companies-cyber/
[7] https://www.theguardian.com/technology/2018/jan/22/cyber-attack-on-uk-matter-of-when-not-if-says-security-chief-ciaran-martin
[9] https://www.theguardian.com/uk-news/2018/apr/12/gchq-chief-jeremy-fleming-reckless-russian-attack-salisbury-skripal
[10] https://www.theguardian.com/uk-news/2018/apr/12/gchq-chief-jeremy-fleming-reckless-russian-attack-salisbury-skripal
[11] http://www.abc.net.au/news/2016-12-10/russia-interfered-in-us-election-to-get-trump-elected-report/8109106
[13] https://www.forbes.com/sites/michaelkrancer/2015/11/04/the-biggest-cybersecurity-threat-the-energy-sector/#25d99cb636ba
[14] https://www.zdnet.com/article/australian-government-considers-approach-to-cybersecurity-world-leading/
[15] http://resources.infosecinstitute.com/cybersecurity-policy-and-threat-assessment-for-the-energy-sector/#gref

